cDFN WatchTower
cDFN WatchTower
cDFN WatchTower
The Next-Generation CAASM
The Next-Generation CAASM
The Next-Generation CAASM
Identify, prioritize, and remediate risks in real-time to strengthen your security posture.
Identify, prioritize, and remediate risks in real-time to strengthen your security posture.

Trusted by




The Full-Stack Approach to CAASM
The Full-Stack Approach to CAASM
The Full-Stack Approach to CAASM
The Full-Stack Approach to CAASM
Our CAASM (Cyber Asset Attack Surface Management) solution integrates risk-based vulnerability management, external attack surface monitoring, dark web surveillance, vendor risk management, and compliance oversight into a single platform. It empowers organizations to proactively identify and address vulnerabilities, secure external assets, monitor potential threats on the dark web, and ensure compliance with industry standards. By consolidating these critical functions, businesses can reduce security gaps, streamline risk management, and enhance overall cybersecurity posture.
Our CAASM (Cyber Asset Attack Surface Management) solution integrates risk-based vulnerability management, external attack surface monitoring, dark web surveillance, vendor risk management, and compliance oversight into a single platform. It empowers organizations to proactively identify and address vulnerabilities, secure external assets, monitor potential threats on the dark web, and ensure compliance with industry standards. By consolidating these critical functions, businesses can reduce security gaps, streamline risk management, and enhance overall cybersecurity posture.
Risk-Based Vulnerability Management
Risk-Based Vulnerability Management
External Attack Surface Management
External Attack Surface Management
Third-Party Risk Management
Third-Party Risk Management
Dark Web Monitoring
Dark Web Monitoring
Compliance management
Compliance management

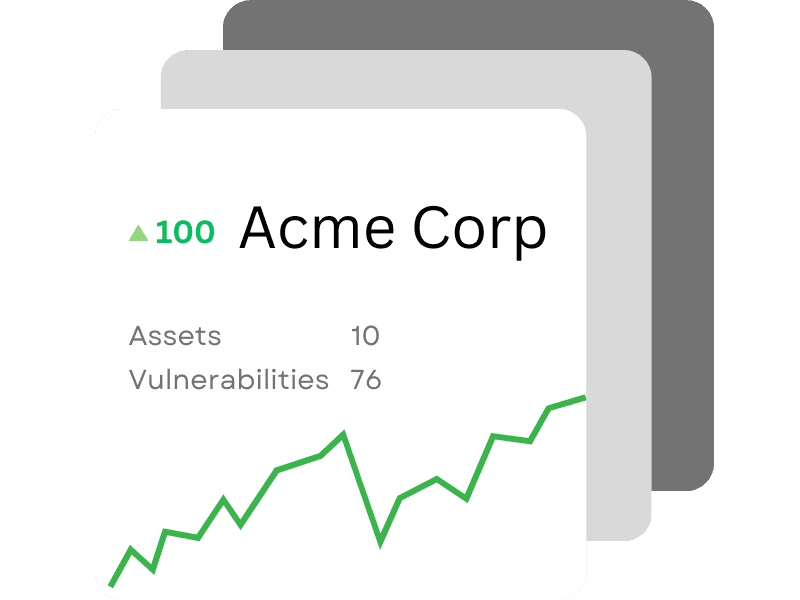
30+ Integrations, 1 Unified View
30+ Integrations, 1 Unified View
30+ Integrations,
1 Unified View
30+ Integrations, 1 Unified View
cDFN WatchTower integrates with 30+ security tools—Vulnerability Management, EDR, DAST, SAST, and more—to provide a unified, comprehensive view of your organization's security posture. By centralizing key insights, cDFN WatchTower streamlines monitoring and response, empowering teams to act faster and more effectively.
cDFN WatchTower integrates with 30+ security tools—Vulnerability Management, EDR, DAST, SAST, and more—to provide a unified, comprehensive view of your organization's security posture. By centralizing key insights, cDFN WatchTower streamlines monitoring and response, empowering teams to act faster and more effectively.



Let’s Talk Unified Organization Security Over Coffee
Let’s Talk Unified Organization Security Over Coffee
Let’s Talk Unified Organization Security Over Coffee
Let’s grab a coffee on us! If you're a security engineer or IT professional at an organization with over 100 employees, we'd love to connect and hear your insights.
Let’s grab a coffee on us! If you're a security engineer or IT professional at an organization with over 100 employees, we'd love to connect and hear your insights.

Managed Security Services
Managed Security Services
Managed Security Services
Managed Security Services provide continuous, 24x7 monitoring through a dedicated Security Operations Center (SOC), ensuring proactive threat detection and rapid response to safeguard your organization around the clock.

Managed Security Services
Managed Security Services provide continuous, 24x7 monitoring through a dedicated Security Operations Center (SOC), ensuring proactive threat detection and rapid response to safeguard your organization around the clock.

Penetration Testing as a Service
Penetration Testing as a Service
Penetration Testing as a Service (PTaaS) offers on-demand, expert-led testing to uncover vulnerabilities, helping you maintain a secure environment with continuous insights and remediation guidance.

Penetration Testing as a Service
Penetration Testing as a Service (PTaaS) offers on-demand, expert-led testing to uncover vulnerabilities, helping you maintain a secure environment with continuous insights and remediation guidance.

Penetration Testing
as a Service
Penetration Testing as a Service (PTaaS) offers on-demand, expert-led testing to uncover vulnerabilities, helping you maintain a secure environment with continuous insights and remediation guidance.

Seamless Integration
Seamless Integration
Seamlessly integrate with over 30+ security tools to unify data and streamline your security operations for enhanced visibility and control.

Seamless Integration
Seamlessly integrate with over 30+ security tools to unify data and streamline your security operations for enhanced visibility and control.

Seamless Integration
Seamlessly integrate with over 30+ security tools to unify data and streamline your security operations for enhanced visibility and control.
Request a Demo
Request a Demo
Request a Demo
Request a Demo
Get a front row seat to the newest in unified security.
Get a front row seat to the newest in unified security.