Risk-Based Vulnerability Management
Optimize your vulnerability management by focusing on the risks that matter most. A risk-first approach prioritizes vulnerabilities based on potential impact, enabling security teams to address high-threat issues efficiently, reduce response times, and strengthen overall cybersecurity defenses.
Optimize your vulnerability management by focusing on the risks that matter most. A risk-first approach prioritizes vulnerabilities based on potential impact, enabling security teams to address high-threat issues efficiently, reduce response times, and strengthen overall cybersecurity defenses.
Optimize your vulnerability management by focusing on the risks that matter most. A risk-first approach prioritizes vulnerabilities based on potential impact, enabling security teams to address high-threat issues efficiently, reduce response times, and strengthen overall cybersecurity defenses.
Risk-Based Vulnerability Management
Risk-Based Vulnerability Management
A Simple Process For Complex Threats
A Simple Process For Complex Threats
A Simple Process For Complex Threats
Aggregate
Unify asset and vulnerability data across critical attack surfaces, covering traditional and cloud infrastructure, as well as application environments. Integrate with 30+ tools to feed exposure findings into a centralized platform.

Aggregate
Unify asset and vulnerability data across critical attack surfaces, covering traditional and cloud infrastructure, as well as application environments. Integrate with 30+ tools to feed exposure findings into a centralized platform.

Correlate
Optimize your asset and vulnerability data by removing duplicates and correlating data, building a holistic asset view and a normalized scoring mechanisms.
Correlate
Optimize your asset and vulnerability data by removing duplicates and correlating data, building a holistic asset view and a normalized scoring mechanisms.

Enrich
Enrich with external threat intelligence sources, incorporating vulnerability severity, exploitability metrics, attack vectors, business context, organizational risk tolerance, and detailed asset data.

Enrich
Enrich with external threat intelligence sources, incorporating vulnerability severity, exploitability metrics, attack vectors, business context, organizational risk tolerance, and detailed asset data.

Proiritize
Prioritize vulnerabilities not just by technical severity but by assessing the genuine cyber risks they pose to your organization. This approach ensures that attention is directed toward vulnerabilities with the most significant potential impact, aligning remediation efforts with real-world threats specific to your environment.
Proiritize
Prioritize vulnerabilities not just by technical severity but by assessing the genuine cyber risks they pose to your organization. This approach ensures that attention is directed toward vulnerabilities with the most significant potential impact, aligning remediation efforts with real-world threats specific to your environment.

Aggregate
Unify asset and vulnerability data across critical attack surfaces, covering traditional and cloud infrastructure, as well as application environments. Integrate with 30+ tools to feed exposure findings into a centralized platform.
Correlate
Optimize your asset and vulnerability data by removing duplicates and correlating data, building a holistic asset view and a normalized scoring mechanisms.
Enrich
Enrich with external threat intelligence sources, incorporating vulnerability severity, exploitability metrics, attack vectors, business context, organizational risk tolerance, and detailed asset data.
Prioritize
Prioritize vulnerabilities not just by technical severity but by assessing the genuine cyber risks they pose to your organization. This approach ensures that attention is directed toward vulnerabilities with the most significant potential impact, aligning remediation efforts with real-world threats specific to your environment.
Transform Vulnerability Management with a Risk-First Approach
Transform Vulnerability Management with a Risk-First Approach
Transform Vulnerability Management with a Risk-First Approach
Transform Vulnerability Management with a Risk-First Approach



Aggregate your data
Aggregate your data
cDFN WatchTower unifies, normalizes, and centralizes data from multiple sources, providing streamlined insights and efficient security management.
- Unified Data Collection
- Real-Time Data Normalization
- Centralized Access
cDFN WatchTower unifies, normalizes, and centralizes data from multiple sources, providing streamlined insights and efficient security management.
- Unified Data Collection
- Real-Time Data Normalization
- Centralized Access
cDFN WatchTower unifies, normalizes, and centralizes data from multiple sources, providing streamlined insights and efficient security management.
- Unified Data Collection
- Real-Time Data Normalization
- Centralized Access
Deepen your insights
Deepen your insights
Deepen your insights
cDFN WatchTower delivers enriched intelligence with precise threat insights, contextual risk scoring, and full attack surface visibility to address vulnerabilities effectively and proactively.
- External Threat Intelligence Integration
- Contextualized Risk Scoring
- Comprehensive Attack Surface Visibility
cDFN WatchTower delivers enriched intelligence with precise threat insights, contextual risk scoring, and full attack surface visibility to address vulnerabilities effectively and proactively.
- External Threat Intelligence Integration
- Contextualized Risk Scoring
- Comprehensive Attack Surface Visibility
cDFN WatchTower delivers enriched intelligence with precise threat insights, contextual risk scoring, and full attack surface visibility to address vulnerabilities effectively and proactively.
- External Threat Intelligence Integration
- Contextualized Risk Scoring
- Comprehensive Attack Surface Visibility



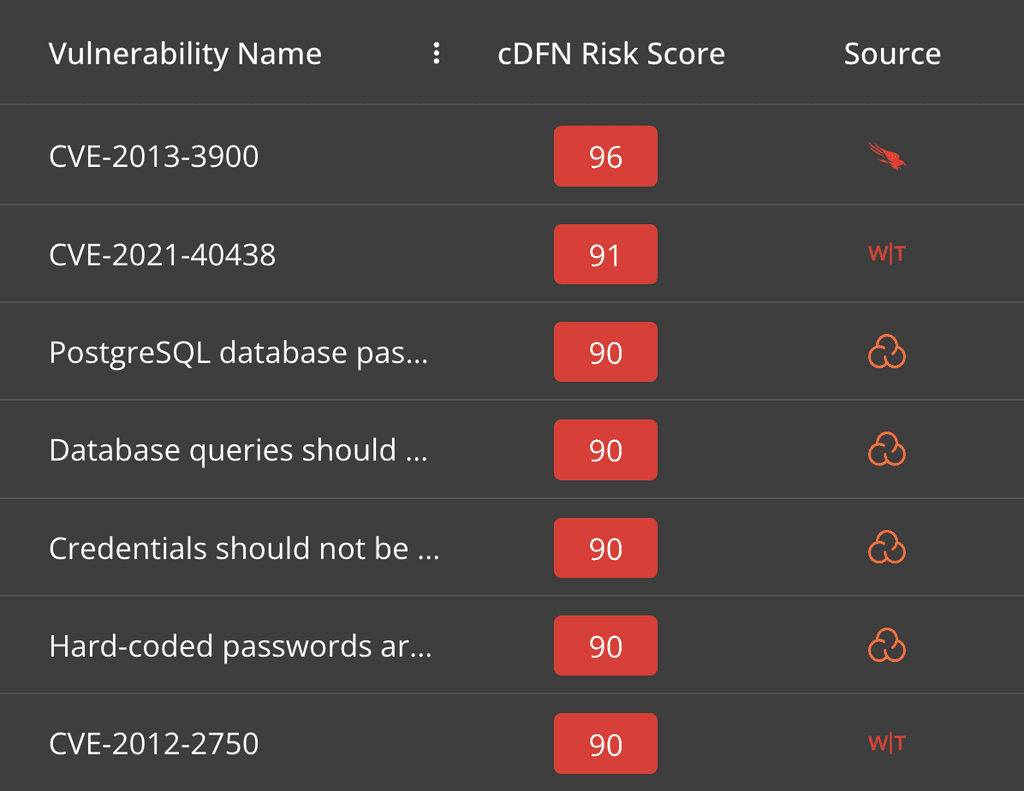


Prioritize your vulnerabilities
Prioritize your vulnerabilities
cDFN WatchTower prioritizes vulnerabilities with risk-based scoring, asset correlation, and guided remediation to help you address high-risk issues efficiently.
- Risk-Based Scoring with Business Context
- Comprehensive Asset and Vulnerability Correlation
- Actionable Insights and Guided Remediation
cDFN WatchTower prioritizes vulnerabilities with risk-based scoring, asset correlation, and guided remediation to help you address high-risk issues efficiently.
- Risk-Based Scoring with Business Context
- Comprehensive Asset and Vulnerability Correlation
- Actionable Insights and Guided Remediation
cDFN WatchTower prioritizes vulnerabilities with risk-based scoring, asset correlation, and guided remediation to help you address high-risk issues efficiently.
- Risk-Based Scoring with Business Context
- Comprehensive Asset and Vulnerability Correlation
- Actionable Insights and Guided Remediation
Seamless Integrations for Enhanced Security
Seamless Integrations for Enhanced Security
Seamless Integrations for Enhanced Security
Seamless Integrations for Enhanced Security
cDFN WatchTower integrates with 30+ security tools—Vulnerability Management, EDR, DAST, SAST, and more—to provide a unified, comprehensive view of your organization's security posture. By centralizing key insights, cDFN WatchTower streamlines monitoring and response, empowering teams to act faster and more effectively.
cDFN WatchTower integrates with 30+ security tools—Vulnerability Management, EDR, DAST, SAST, and more—to provide a unified, comprehensive view of your organization's security posture. By centralizing key insights, cDFN WatchTower streamlines monitoring and response, empowering teams to act faster and more effectively.
cDFN WatchTower integrates with 30+ security tools—Vulnerability Management, EDR, DAST, SAST, and more—to provide a unified, comprehensive view of your organization's security posture. By centralizing key insights, cDFN WatchTower streamlines monitoring and response, empowering teams to act faster and more effectively.
See cDFN WatchTower in action
See cDFN WatchTower in action
See cDFN WatchTower
in action
Get a front row seat to the newest in unified security.
Get a front row seat to the newest in unified security.