External Attack Surface Management
cDFN WatchTower's External Attack Surface Management provides continuous visibility and monitoring of your organization's external-facing assets, identifying vulnerabilities and exposures across traditional and cloud environments. By proactively scanning and analyzing potential attack vectors, it helps secure all entry points and reduces risk from external threats.
cDFN WatchTower's External Attack Surface Management provides continuous visibility and monitoring of your organization's external-facing assets, identifying vulnerabilities and exposures across traditional and cloud environments. By proactively scanning and analyzing potential attack vectors, it helps secure all entry points and reduces risk from external threats.
cDFN WatchTower's External Attack Surface Management provides continuous visibility and monitoring of your organization's external-facing assets, identifying vulnerabilities and exposures across traditional and cloud environments. By proactively scanning and analyzing potential attack vectors, it helps secure all entry points and reduces risk from external threats.
External Attack Surface Management
External Attack Surface Management
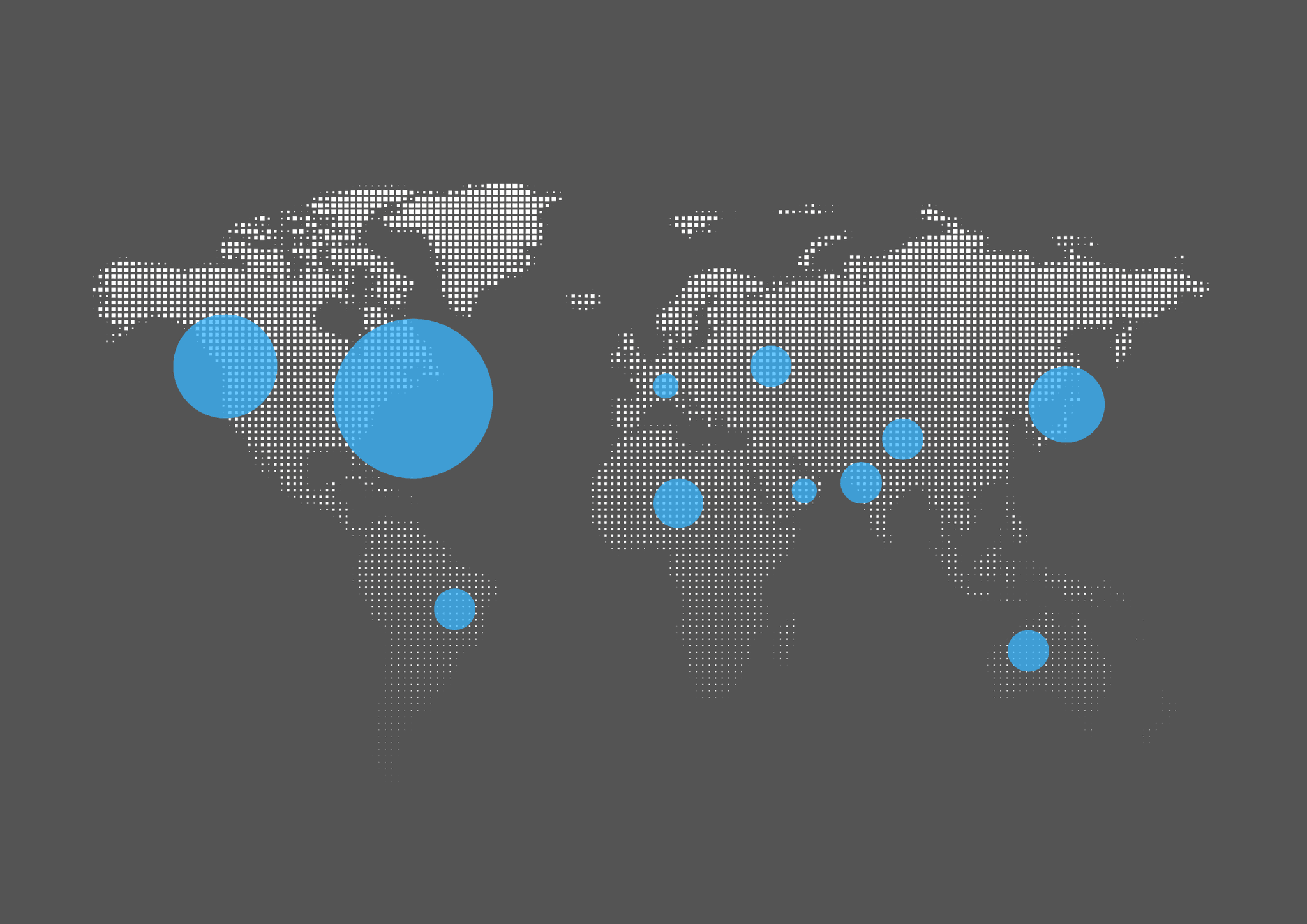
Real-Time Monitoring of Your Attack Surface
Real-Time Monitoring of Your Attack Surface
Real-Time Monitoring of Your Attack Surface



Web Application Scanner
Web Application Scanner
Identify vulnerabilities in your web applications, including SQL injection, XSS, and other common threats, to ensure strong and reliable security.
Identify vulnerabilities in your web applications, including SQL injection, XSS, and other common threats, to ensure strong and reliable security.
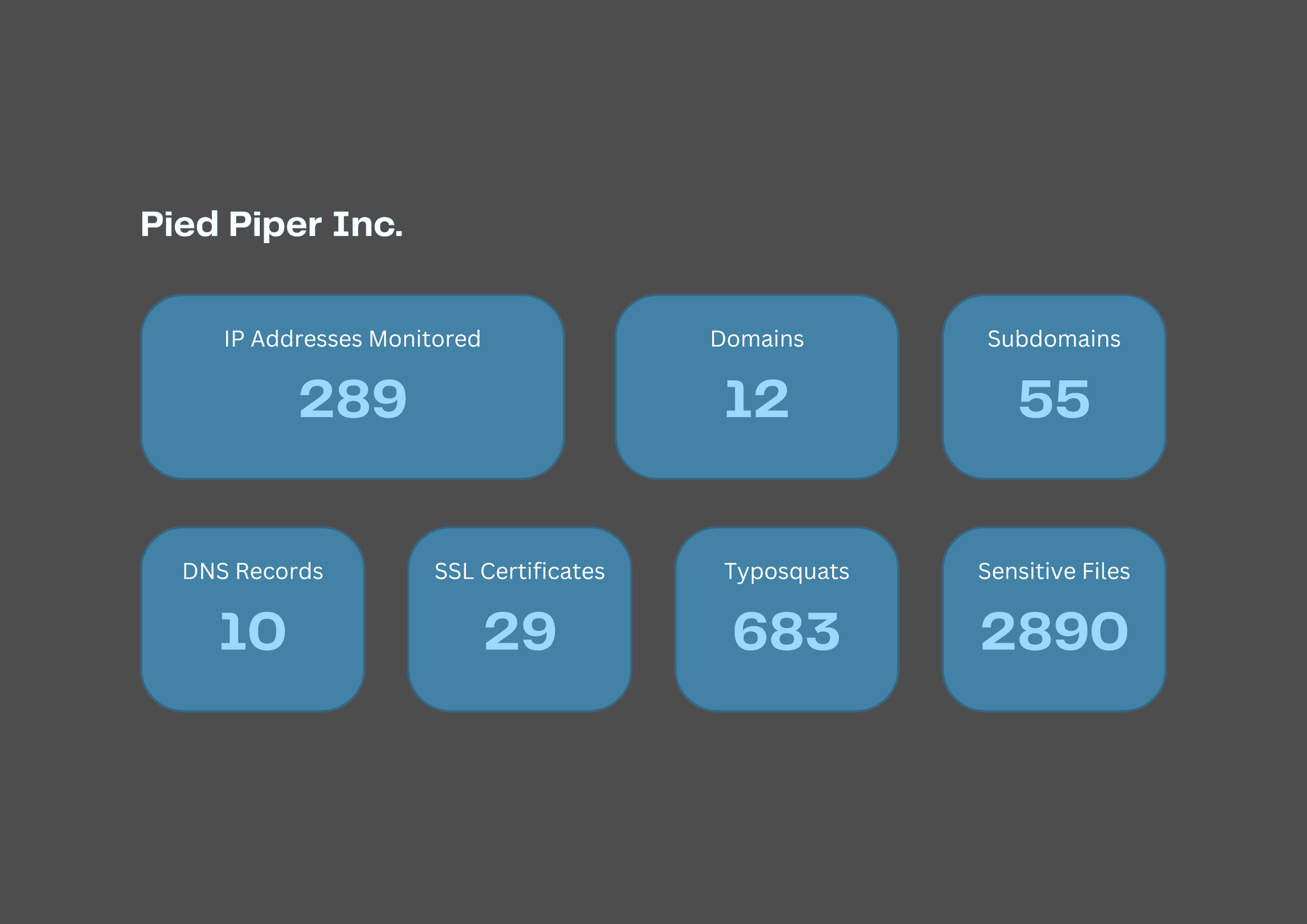


Continuous Discovery of Your Digital Infrastructure
Continuous Discovery of Your Digital Infrastructure
Easily identify and catalog all external assets, technologies, and software with automated discovery. cDFN WatchTower continuously scans your digital environment, providing an up-to-date inventory for improved risk assessment and asset management across all platforms.
Easily identify and catalog all external assets, technologies, and software with automated discovery. cDFN WatchTower continuously scans your digital environment, providing an up-to-date inventory for improved risk assessment and asset management across all platforms.


Minimize Your Attack Surface
Minimize Your Attack Surface
Minimize your attack surface by identifying software vulnerabilities and detecting domain permutations prone to typosquatting. With continuous scanning, cDFN WatchTower alerts you to new vulnerabilities as they emerge, allowing for swift action to close potential risks and strengthen defenses.
Minimize your attack surface by identifying software vulnerabilities and detecting domain permutations prone to typosquatting. With continuous scanning, cDFN WatchTower alerts you to new vulnerabilities as they emerge, allowing for swift action to close potential risks and strengthen defenses.



Brand Monitoring
Brand Monitoring
Monitor your brand’s digital presence to detect unauthorized use, impersonation, and potential threats, helping you protect brand integrity and reputation.
Monitor your brand’s digital presence to detect unauthorized use, impersonation, and potential threats, helping you protect brand integrity and reputation.
All your Attack Surface Management needs in one place
All your Attack Surface Management needs in one place
All your Attack Surface Management needs in one place
Assets, Technology and Software Detection
Automatically discover and catalog all external assets, technologies, and software for complete visibility and improved security management across your digital environment.
Automatically discover and catalog all external assets, technologies, and software for complete visibility and improved security management across your digital environment.
Vulnerability Detection
Continuously identify and assess system vulnerabilities, providing insights for proactive remediation and strengthened security.
Continuously identify and assess system vulnerabilities, providing insights for proactive remediation and strengthened security.
SSL Scanning
Monitor and analyze SSL certificates across your digital environment to detect vulnerabilities, expired certificates, and misconfigurations. SSL Scanning ensures secure connections and helps maintain a strong, trusted security posture.
Monitor and analyze SSL certificates across your digital environment to detect vulnerabilities, expired certificates, and misconfigurations. SSL Scanning ensures secure connections and helps maintain a strong, trusted security posture.
DNS Scanning
Continuously monitor and analyze DNS records to detect vulnerabilities, misconfigurations, and unauthorized changes. DNS Scanning helps secure your domain, prevent spoofing, and maintain a resilient online presence.
Continuously monitor and analyze DNS records to detect vulnerabilities, misconfigurations, and unauthorized changes. DNS Scanning helps secure your domain, prevent spoofing, and maintain a resilient online presence.
OWASP Top 10 Scanning
Scan for critical web application vulnerabilities listed in the OWASP Top 10 to protect against common threats and enhance security.
Scan for critical web application vulnerabilities listed in the OWASP Top 10 to protect against common threats and enhance security.
Typosquat Domain Detection
Identify and monitor domains that mimic your brand through slight misspellings or variations to prevent phishing, fraud, and brand impersonation. Typosquat detection safeguards your brand’s integrity and helps protect users from malicious sites.
Identify and monitor domains that mimic your brand through slight misspellings or variations to prevent phishing, fraud, and brand impersonation. Typosquat detection safeguards your brand’s integrity and helps protect users from malicious sites.
Exposed Sensitive Documents Detection
Identify and monitor exposed sensitive documents across public sources to prevent data leaks and protect valuable information from unauthorized access.
Identify and monitor exposed sensitive documents across public sources to prevent data leaks and protect valuable information from unauthorized access.
Brand Monitoring
Track your brand’s online presence to detect unauthorized use, impersonation, and potential threats, helping protect your reputation and maintain brand integrity.
Track your brand’s online presence to detect unauthorized use, impersonation, and potential threats, helping protect your reputation and maintain brand integrity.
Monitor your Attack Surface Today
Monitor your Attack Surface Today
Monitor your Attack Surface Today
Get a front row seat to the newest in unified security.
Get a front row seat to the newest in unified security.