Third-Party Risk Management
Identify, evaluate, and manage risks across your entire vendor ecosystem with the powerful capabilities of cDFN WatchTower. From onboarding assessments to continuous monitoring, cDFN WatchTower provides a comprehensive view of each vendor’s security posture, helping you detect vulnerabilities, data leaks, and compliance gaps before they impact your organization.
Identify, evaluate, and manage risks across your entire vendor ecosystem with the powerful capabilities of cDFN WatchTower. From onboarding assessments to continuous monitoring, cDFN WatchTower provides a comprehensive view of each vendor’s security posture, helping you detect vulnerabilities, data leaks, and compliance gaps before they impact your organization.
Identify, evaluate, and manage risks across your entire vendor ecosystem with the powerful capabilities of cDFN WatchTower. From onboarding assessments to continuous monitoring, cDFN WatchTower provides a comprehensive view of each vendor’s security posture, helping you detect vulnerabilities, data leaks, and compliance gaps before they impact your organization.
Third-Party Risk Management
Third-Party Risk Management
Identify and Mitigate Vendor Risks
Identify and Mitigate Vendor Risks
Identify and Mitigate Vendor Risks



Automated Vendor Assessments
Automated Vendor Assessments
Automatically assess vendors based on their security posture, gathering insights into critical vulnerabilities and potential exposure.
Automatically assess vendors based on their security posture, gathering insights into critical vulnerabilities and potential exposure.
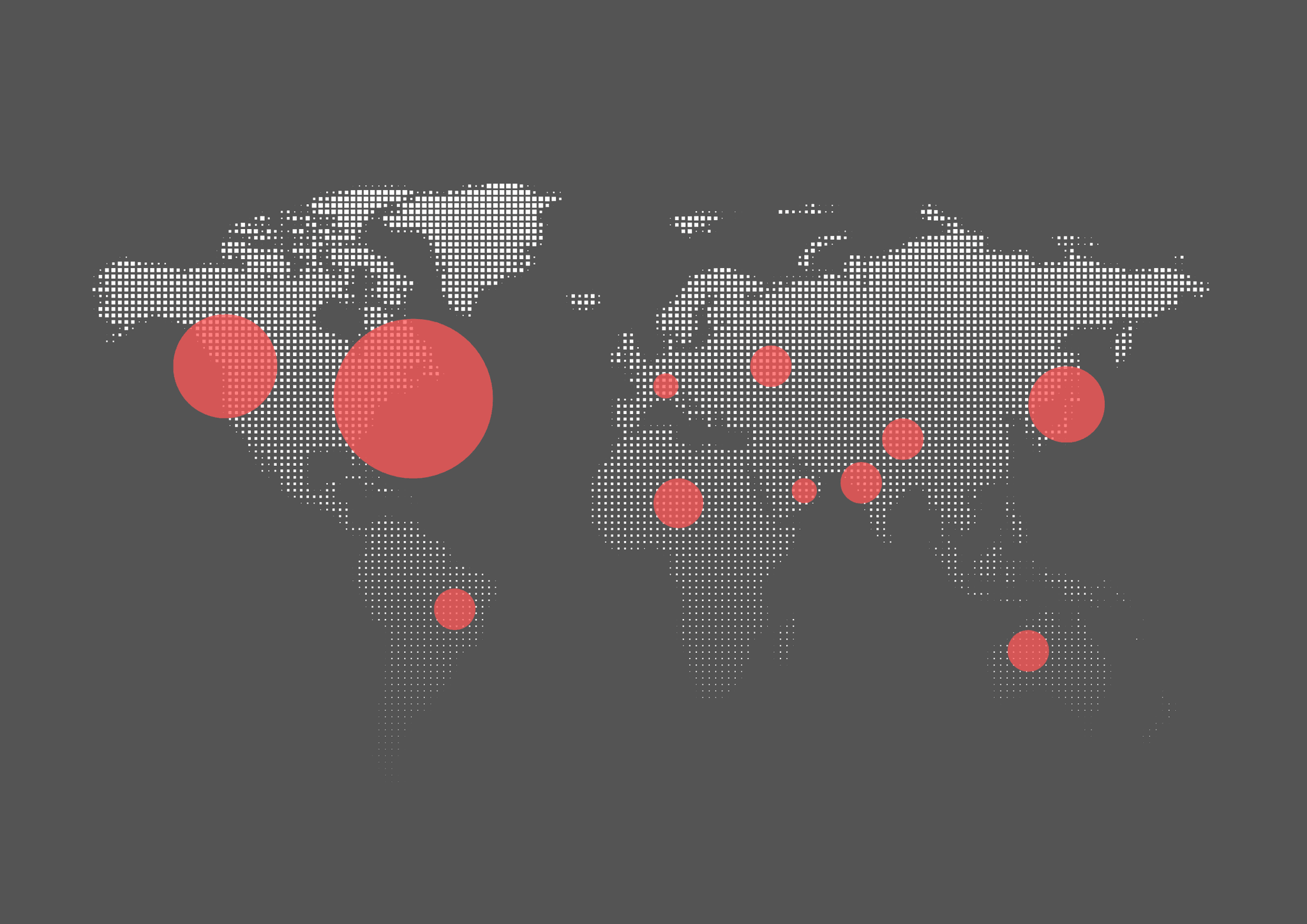


Real-Time Threat Monitoring
Real-Time Threat Monitoring
Monitor vendor environments for real-time threats, breaches, and cyber incidents that may impact your organization.
Monitor vendor environments for real-time threats, breaches, and cyber incidents that may impact your organization.
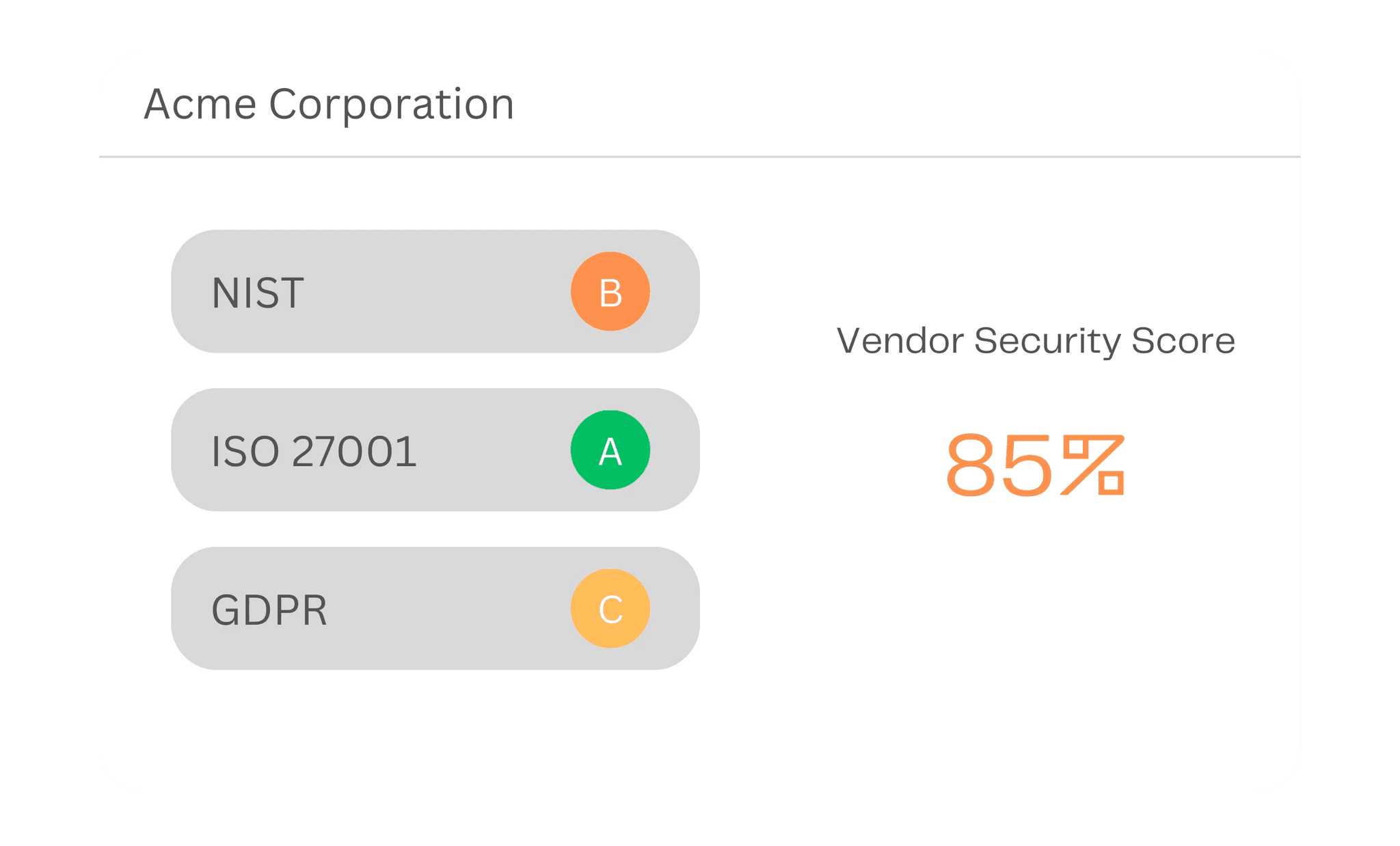


Regulatory Compliance Checks
Regulatory Compliance Checks
Automate compliance assessments aligned with NIST, ISO 27001, and other regulatory frameworks to maintain third-party compliance standards.
Automate compliance assessments aligned with NIST, ISO 27001, and other regulatory frameworks to maintain third-party compliance standards.



Comprehensive Security Scoring
Comprehensive Security Scoring
Evaluate and track your vendors' overall security posture with cDFN’s proprietary security and ransomware risk scores, helping prioritize risks by severity.
Evaluate and track your vendors' overall security posture with cDFN’s proprietary security and ransomware risk scores, helping prioritize risks by severity.
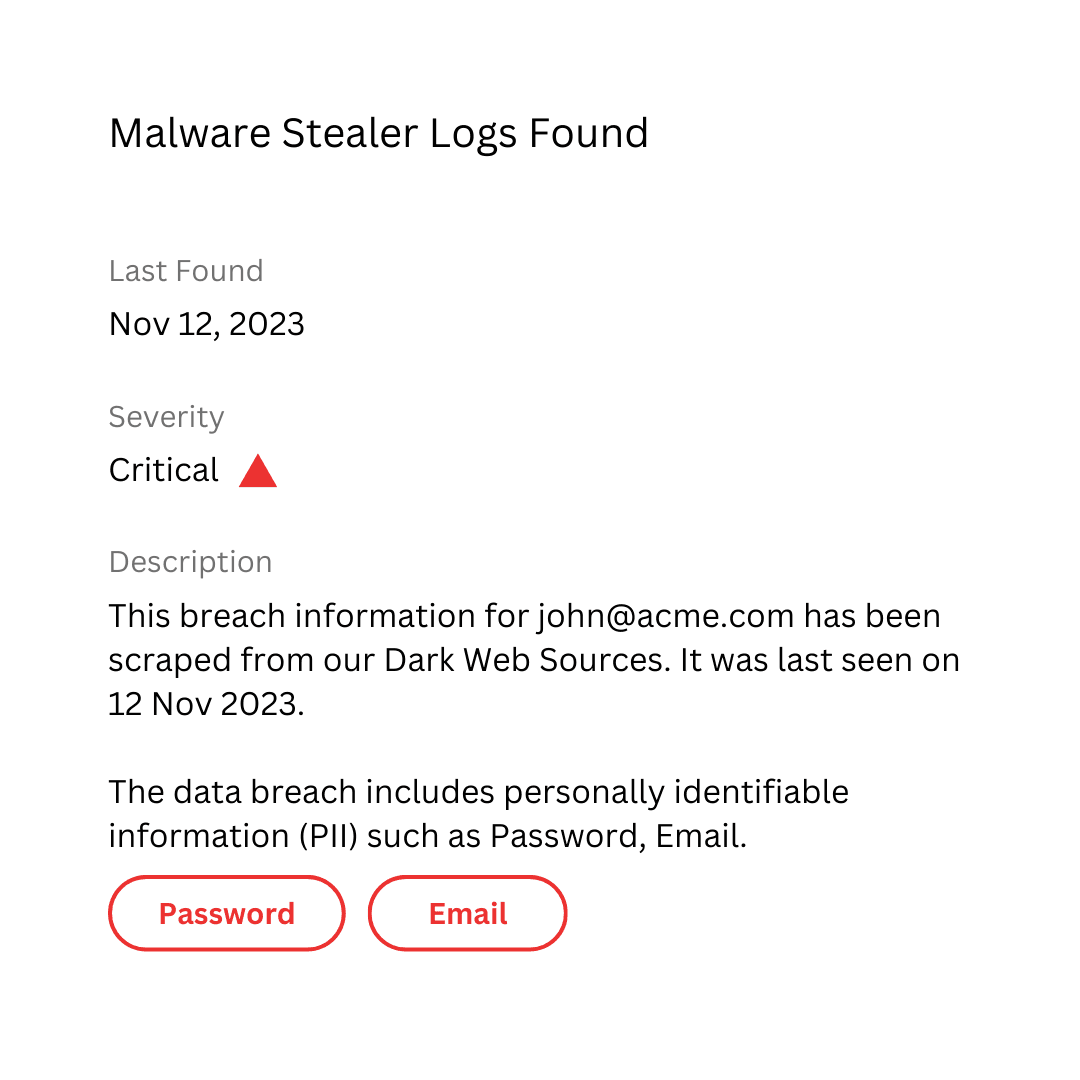


Vendor Dark Web Monitoring
Vendor Dark Web Monitoring
Identify vendor data leaks on the dark web, from compromised credentials to sensitive PII, ensuring proactive risk management.
Identify vendor data leaks on the dark web, from compromised credentials to sensitive PII, ensuring proactive risk management.
A Four-Step Approach to Comprehensive Third-Party Risk Management
A Four-Step Approach to Comprehensive Third-Party Risk Management
A Four-Step Approach to Comprehensive Third-Party Risk Management
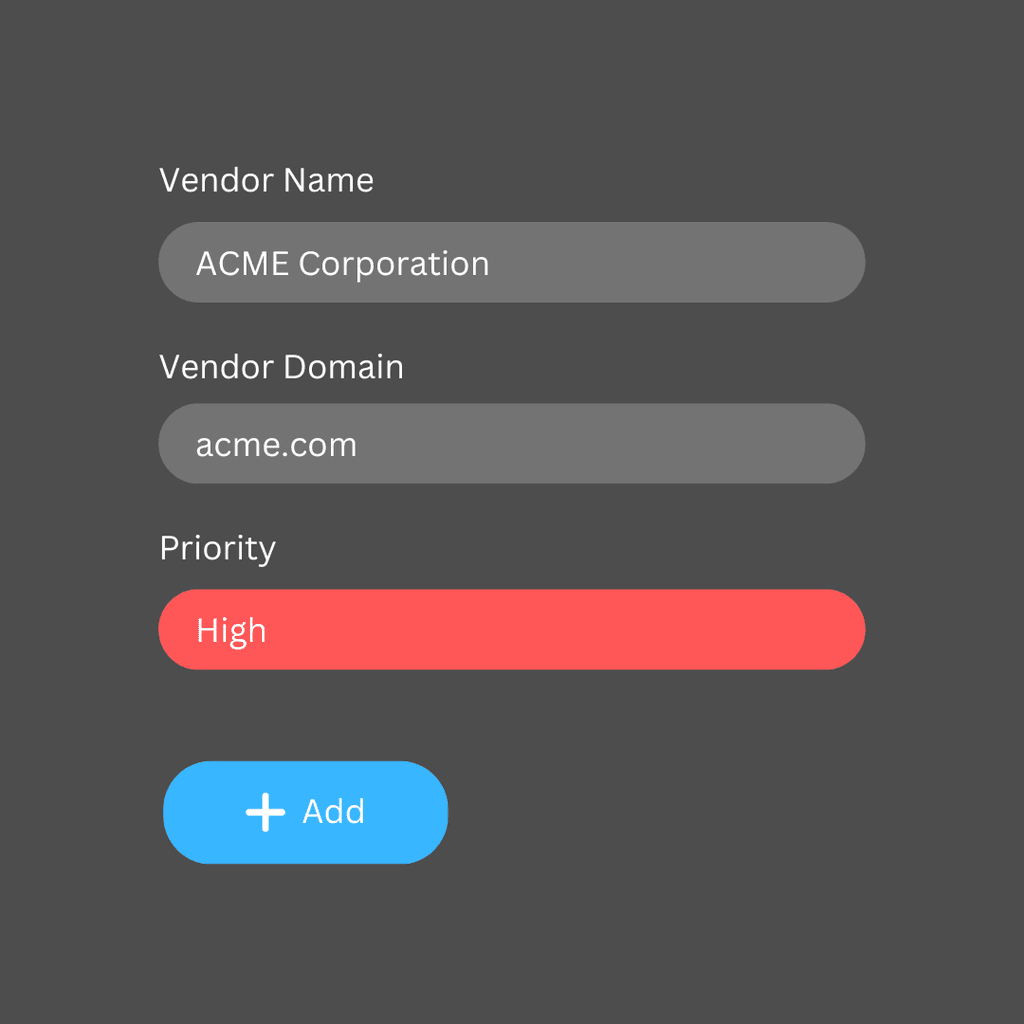
Vendor Assessment and Onboarding
Start with an automated risk assessment of each vendor to understand potential vulnerabilities. Use cDFN WatchTower’s insights to evaluate vendors based on their risk factors, security posture, and compliance standards.
Continuous Monitoring and Threat Alerts
cDFN WatchTower continuously monitors third-party environments, identifying high-risk vulnerabilities, data breaches, and dark web leaks relevant to your vendors.
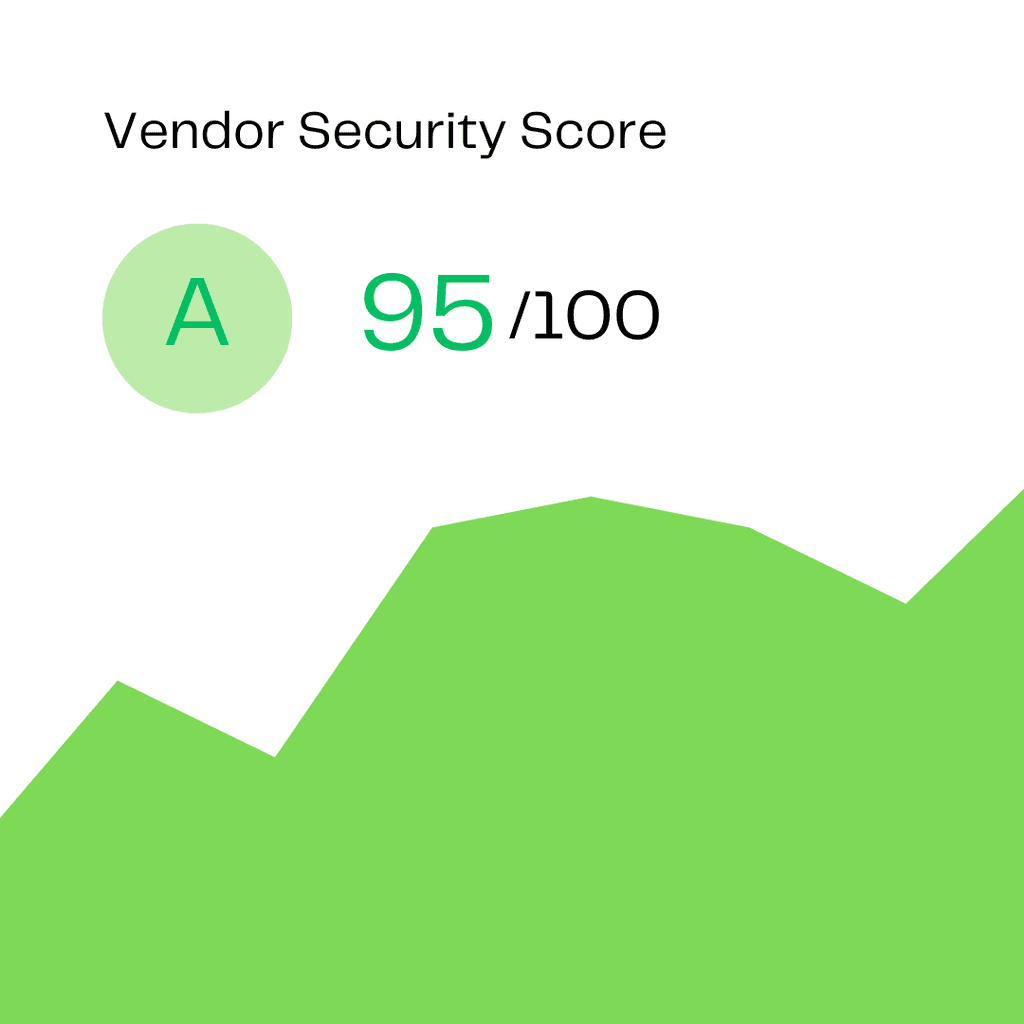

Risk Scoring and Prioritization
With an advanced security scoring model, prioritize vendors by their overall risk score and focus on those with the highest vulnerability to incidents like ransomware attacks.
Reporting and Compliance Management
Generate comprehensive reports with insights into each vendor’s risk level and compliance status, making it easy to meet regulatory requirements and ensure third-party accountability.



Vendor Assessment and Onboarding
Start with an automated risk assessment of each vendor to understand potential vulnerabilities. Use cDFN WatchTower’s insights to evaluate vendors based on their risk factors, security posture, and compliance standards.
Continuous Monitoring and Threat Alerts
cDFN WatchTower continuously monitors third-party environments, identifying high-risk vulnerabilities, data breaches, and dark web leaks relevant to your vendors.


Reporting and Compliance Management
Generate comprehensive reports with insights into each vendor’s risk level and compliance status, making it easy to meet regulatory requirements and ensure third-party accountability.




Risk Scoring and Prioritization
With an advanced security scoring model, prioritize vendors by their overall risk score and focus on those with the highest vulnerability to incidents like ransomware attacks.


Vendor Assessment and Onboarding
Start with an automated risk assessment of each vendor to understand potential vulnerabilities. Use cDFN WatchTower’s insights to evaluate vendors based on their risk factors, security posture, and compliance standards.


Continuous Monitoring and Threat Alerts
cDFN WatchTower continuously monitors third-party environments, identifying high-risk vulnerabilities, data breaches, and dark web leaks relevant to your vendors.


Risk Scoring and Prioritization
With an advanced security scoring model, prioritize vendors by their overall risk score and focus on those with the highest vulnerability to incidents like ransomware attacks.


Reporting and Compliance Management
Generate comprehensive reports with insights into each vendor’s risk level and compliance status, making it easy to meet regulatory requirements and ensure third-party accountability.
Explore Third-Party Risk Management in Action
Explore Third-Party Risk Management in Action
Explore Third-Party Risk Management in Action
See how cDFN WatchTower can help you take control of your vendor ecosystem, prioritize security efforts, and ensure compliance.
See how cDFN WatchTower can help you take control of your vendor ecosystem, prioritize security efforts, and ensure compliance.